Snow Risk Monitor
Mitigate surface IT risks effectively with Snow
99% of exploited vulnerabilities are ones known to security and IT professionals. Snow Risk Monitor provides the visibility to prioritize how to address these risks based on vulnerability severity and personally identifiable information (PII) exposure.
Recommended Solutions
Manage risk with a comprehensive view of vulnerabilities
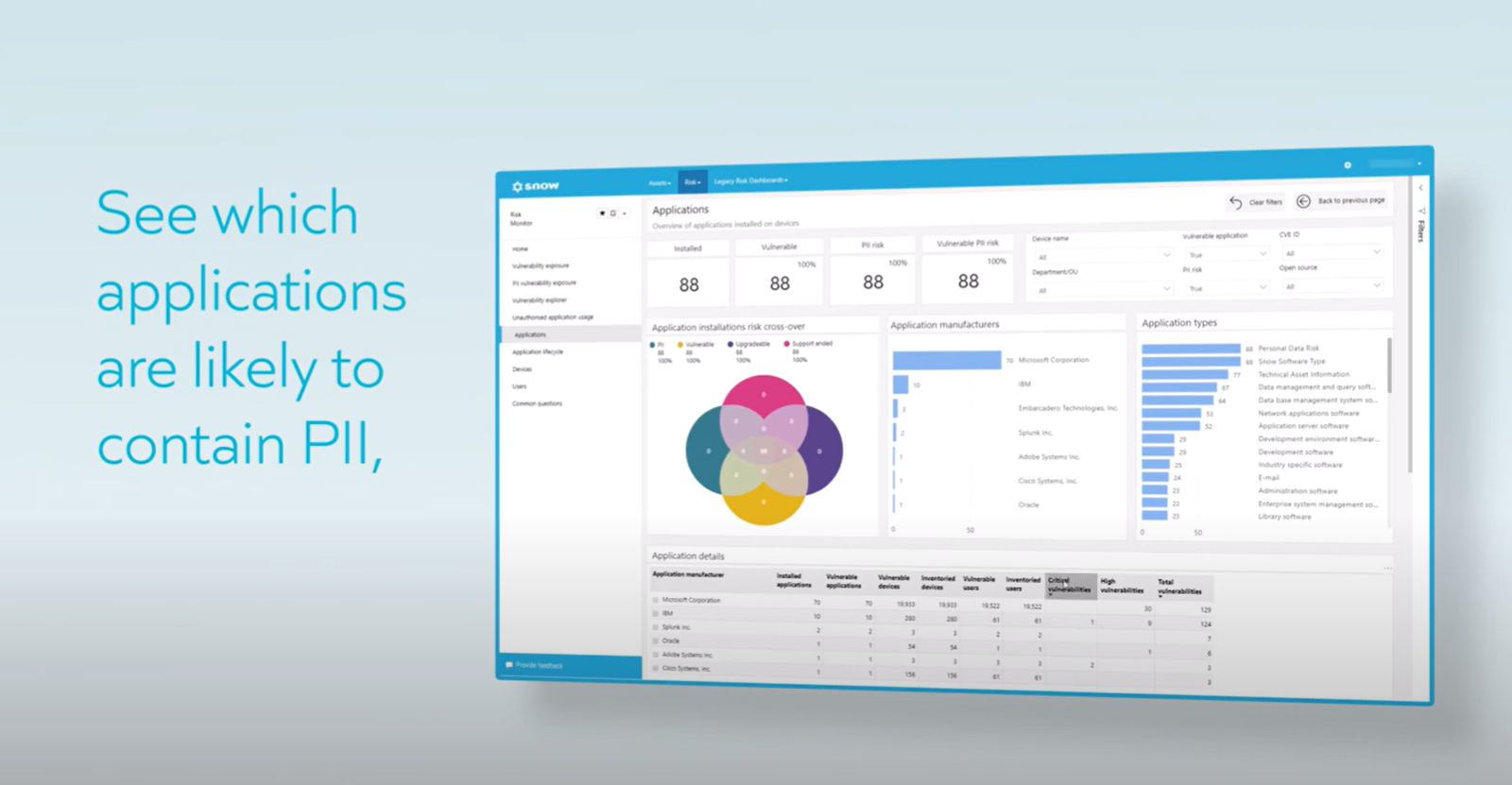
Identify vulnerabilities
Find applications with vulnerabilities in your environment
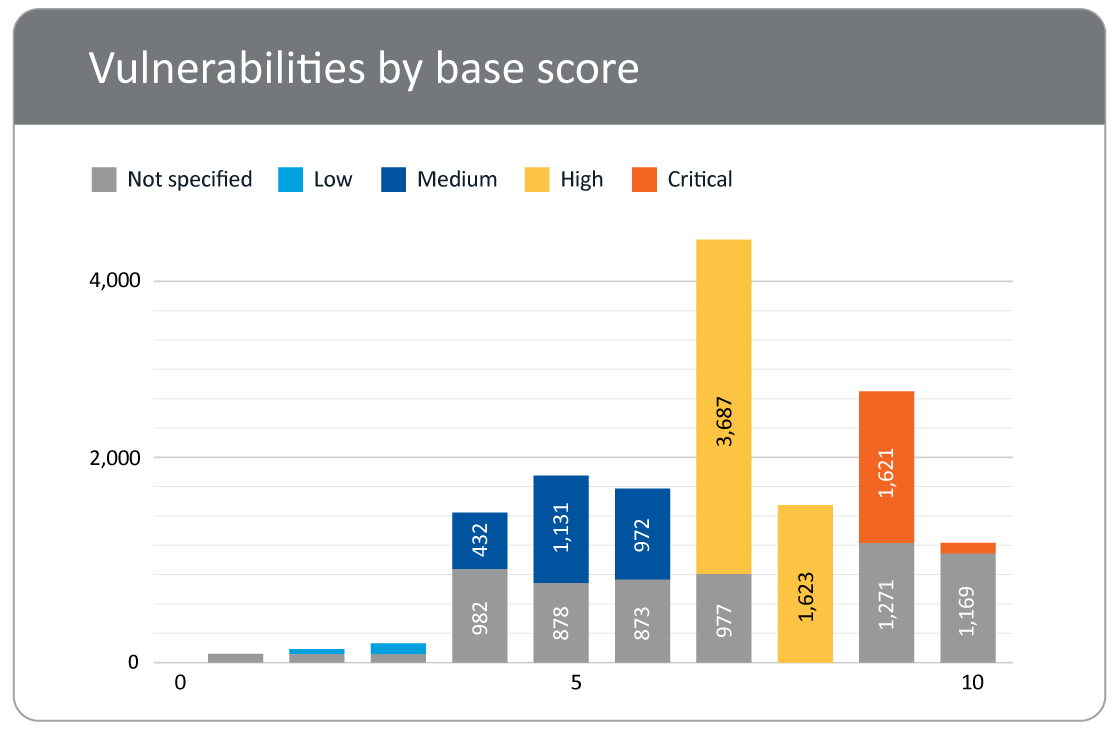
Hackers exploit vulnerabilities both new and old and with AI, threat actors have advanced tools at their disposal. You can't afford to have unpatched vulnerabilities in your environment. Snow Risk Monitor surfaces all vulnerabilities through our integration with the NVD database and marries this information with your Snow inventory data to show you where there are vulnerabilities that need to be immediately patched.
Prioritize remediation
Patch, update or remove the riskiest applications first
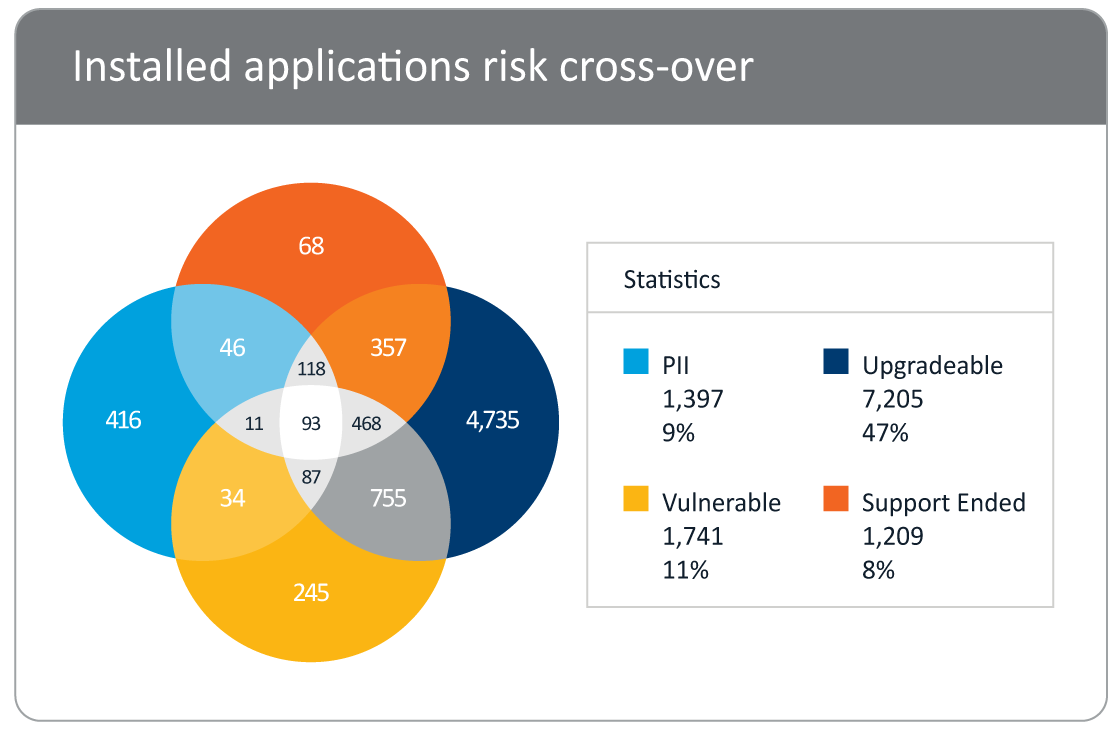
Once you’ve identified that risks are present, it’s time to prioritize what to address first. Snow Risk Monitor helps by providing robust, contextual data around those risks, so you can determine what’s a high priority for your organization such as:
- Risks with a critical vulnerability
- Risks with applications no longer supported
- Risks on devices with high profile users
Report progress
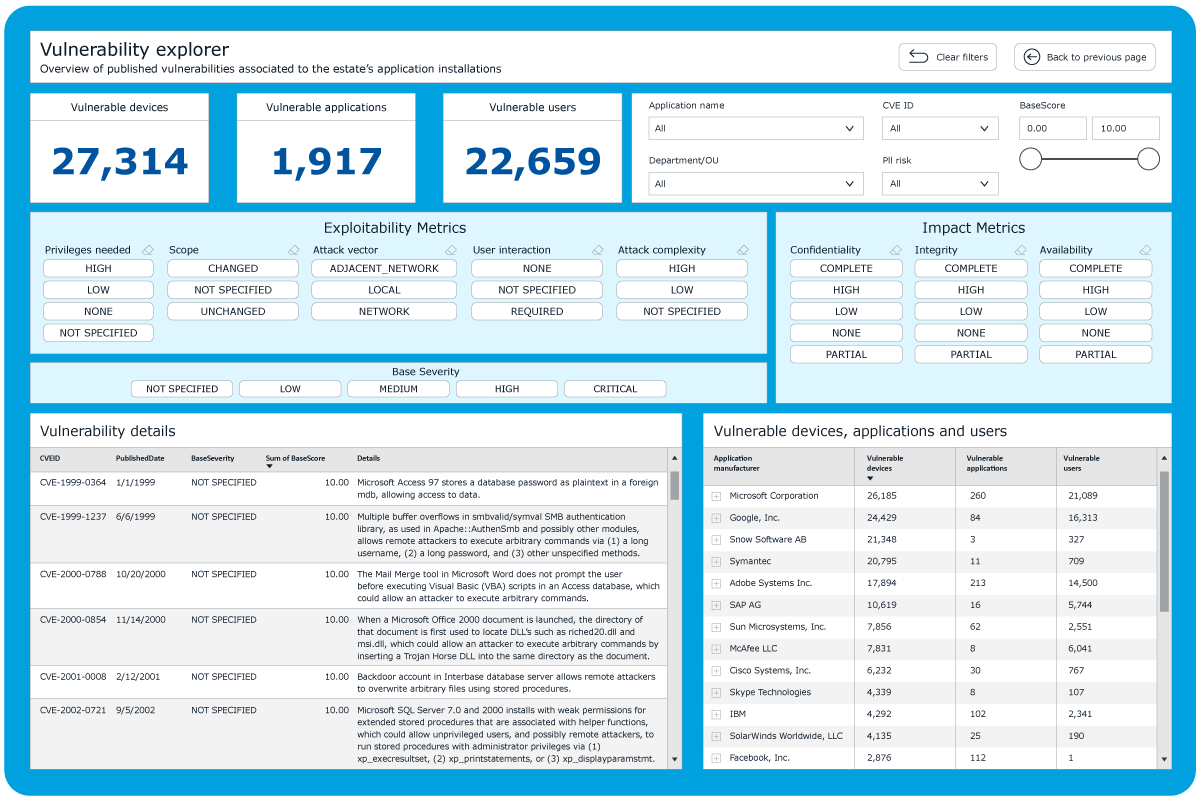
Measure progress against patching vulnerabilities and removing EOL/EOS risk
The interactive dashboard allows you to fully understand the risk landscape and make informed decisions about mitigation. Export your search results so you can share them with other teams and integrate with remediation tools, security planning and more.
It takes just 14 days
for an exploit to be available in the wild after a vulnerability has been publicly disclosed
How it Works
Detailed visibility to prioritize threat defense
Snow Risk Monitor provides complete visibility of all devices, users and applications. Automated discovery provides a detailed account of which users have access to which applications and how they are used. Snow Risk Monitor shows which vulnerable applications are in use and where they reside and identifies attack vectors of the path of a vulnerability. Applications are also classified to highlight where personal data could be stored and processed.
When you install Snow, you have a lights on moment and all of the sudden you see everything and it’s scary. Exciting and scary as well, but it gives you that visibility. You can actually see what you have on your estate, who’s got it, how they’re using it and when they’re using it, and it makes a massive difference.
Frequently asked questions
Risk Monitor provides detailed information regarding the inventory of devices, both normalized and in raw data formats. In addition, Risk Monitor provides complete visibility of all devices, users and applications. Automated discovery provides a detailed account of which users have access to which applications, and how they are used. Snow Risk Monitor helps mitigate cyber security risks by checking all applications against the best vulnerability information available – the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) – and flagging those with known vulnerabilities. Benefits include:
- Find all known vulnerabilities – not just the ones in the big data processing applications
- See which vulnerable applications are in use and where they reside in your estate
- Review upcoming End-of-Life and End-of-Support dates to minimize risk and maintain compliance
- Prioritize remediation efforts based on NVD severity level
- Quickly identify possible data leaks
- Identify applications processing personal data
- Know which applications are installed on each device and who has access to them
- See the severity level of identified risks based on augmented data sets
Risk Monitor helps prioritize risk by understanding the different versions and editions of software deployed across different organization divisions. This can also be considered a risk related to the cost and effort for the IT organization to operate and support all these variants of the software. It’s best practice to standardize on fewer versions, in order to improve productivity and support efforts.
With this data, Snow Risk Monitor also helps identify vulnerable applications and applications nearing or already at end of life and end of support.
Additionally, other solutions on Snow Atlas help organizations assess audit/legal risk by understanding current license compliance, financial risk by understanding underutilized licenses and applications, and security risk for applications being used but on the deny list or those not yet vetted by IT security.
Yes, Risk Monitor is hosted in the cloud on Microsoft Azure, which provides scalable data processing to combine data from our rich Data Intelligence Service and the NVD (NIST) datasets. Please see the Risk Monitor documentation for an overview of its architecture.
INFORMING IT, TRANSFORMING IT
Industry insights to help keep you informed
Let’s get started
Our team is standing by to discuss your requirements and deliver a demo of our industry-leading platform.